2025.7.7
2025
Software Engneering
2025 ASE Journal (ASE)
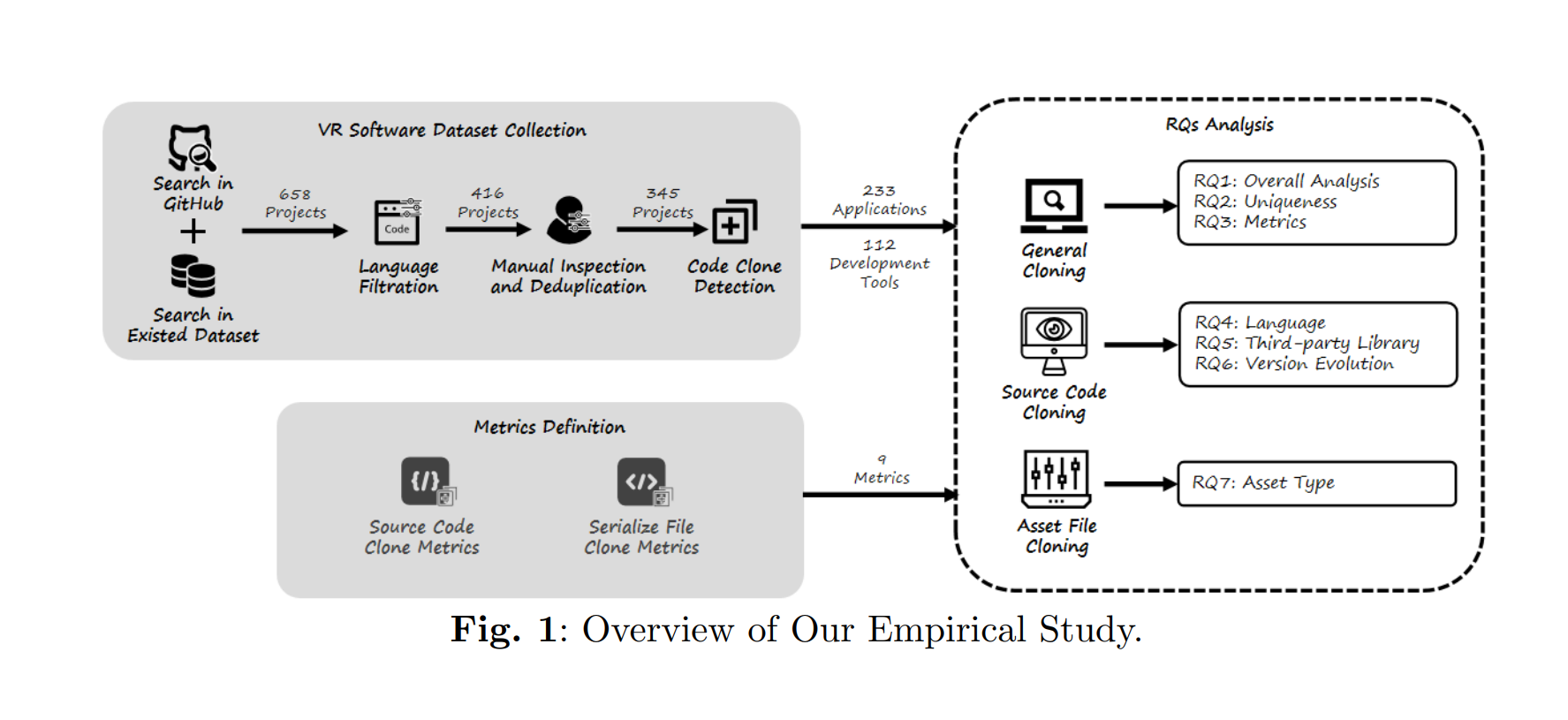
Unveiling Code Clone Patterns in Open Source VR Software: An Empirical StudyHuashan Chen, Zisheng Huang, Yifan Xu, Wenjie Huang, Xuheng Wang, Jinfu Chen, Haotang Li, Kebin Peng, Feng Liu, Sen He
Security
IEEE Transactions on Information Forensics & Security (TIFS)
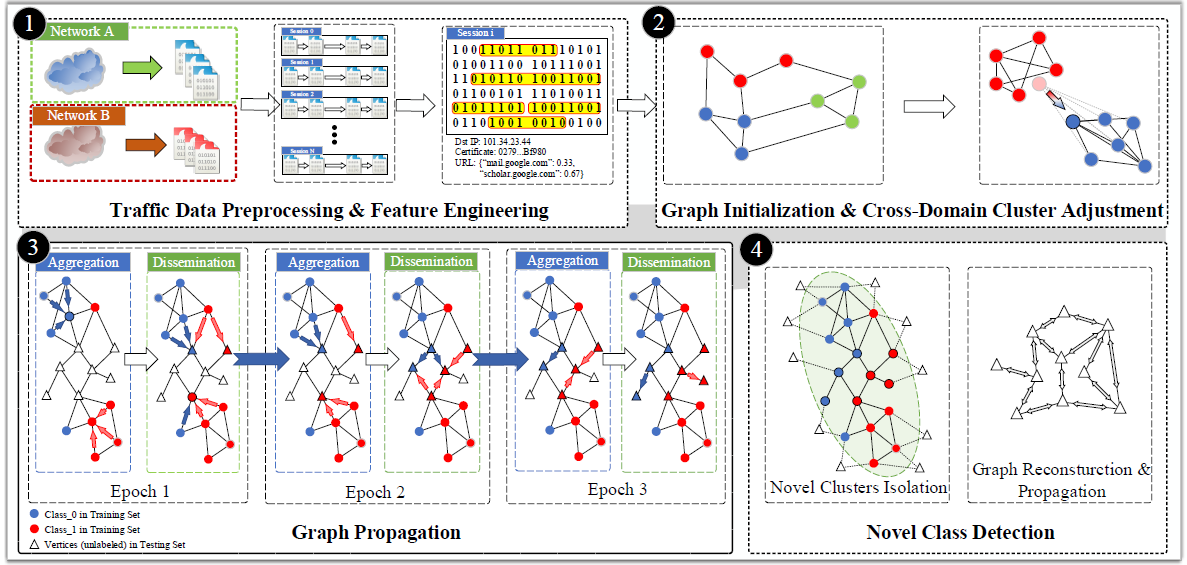
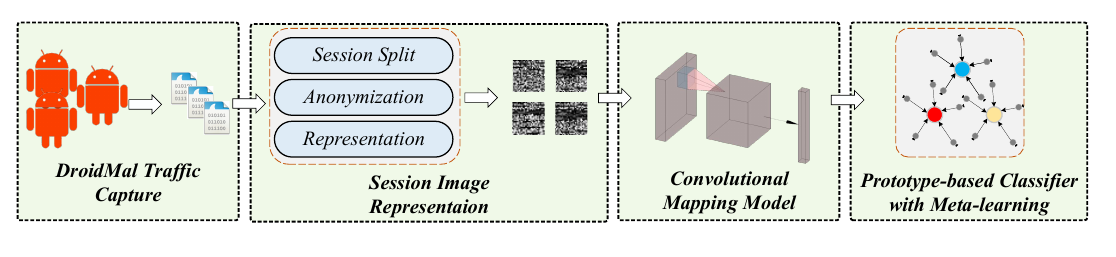
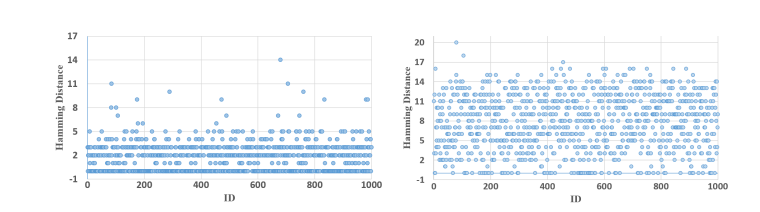
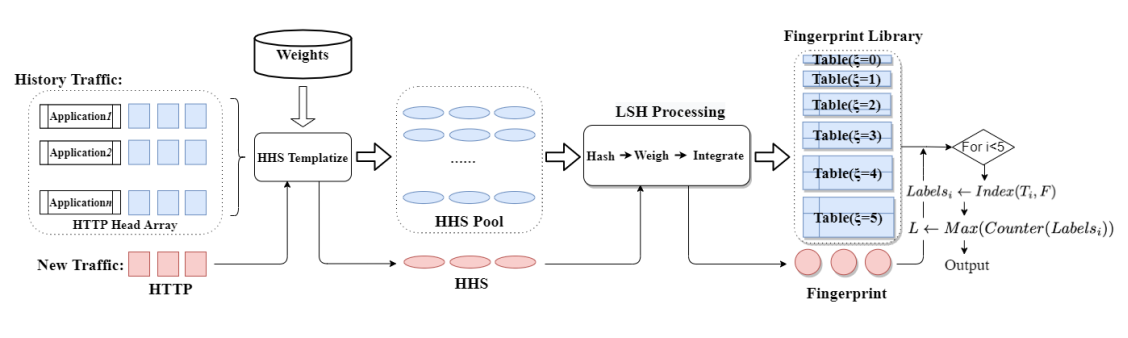
Magnifier: Detecting Network Access via Lightweight Traffic-based FingerprintsWenhao Li, Qiang Wang, Huaifeng Bao, Xiao-Yu Zhang, Lingyun Ying, Zhaoxuan Li, Huamin Jin, Shuai Wang
2025.07.07
Security
The 33rd ACM International Conference on Multimedia (MM)
Knowledge Negative Distillation: Circumventing Overfitting to Unlock More Generalizable Deepfake DetectionJipeng Liu, Haichao Shi, Yaru Zhang, Xiaoyu Zhang
2025.07.05
Intrusion Detection; Network Security
2025 IEEE Transactions on Networking (TON 2025) (TON)
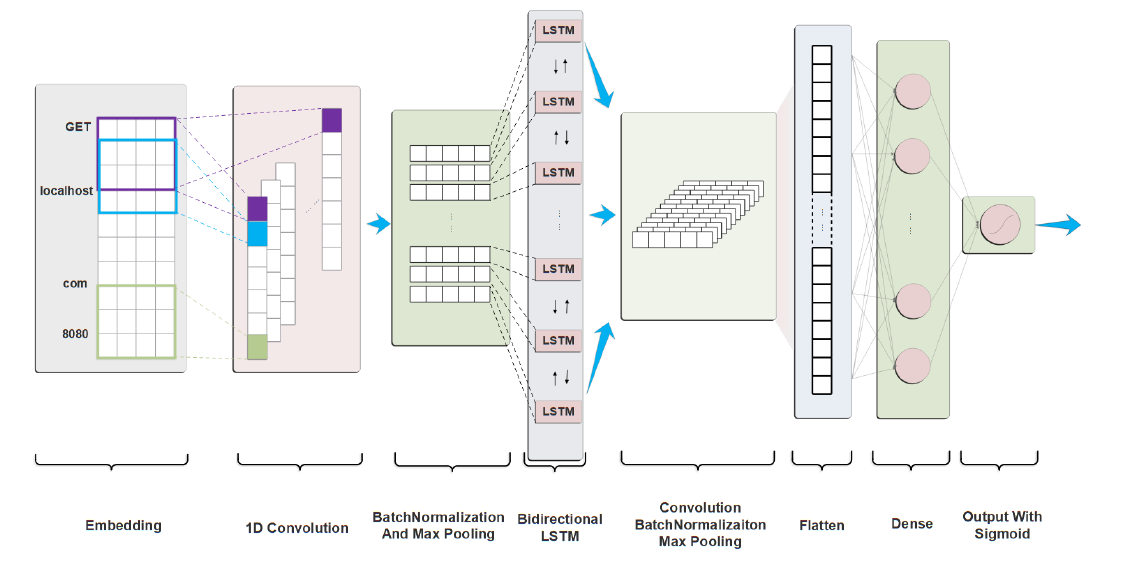
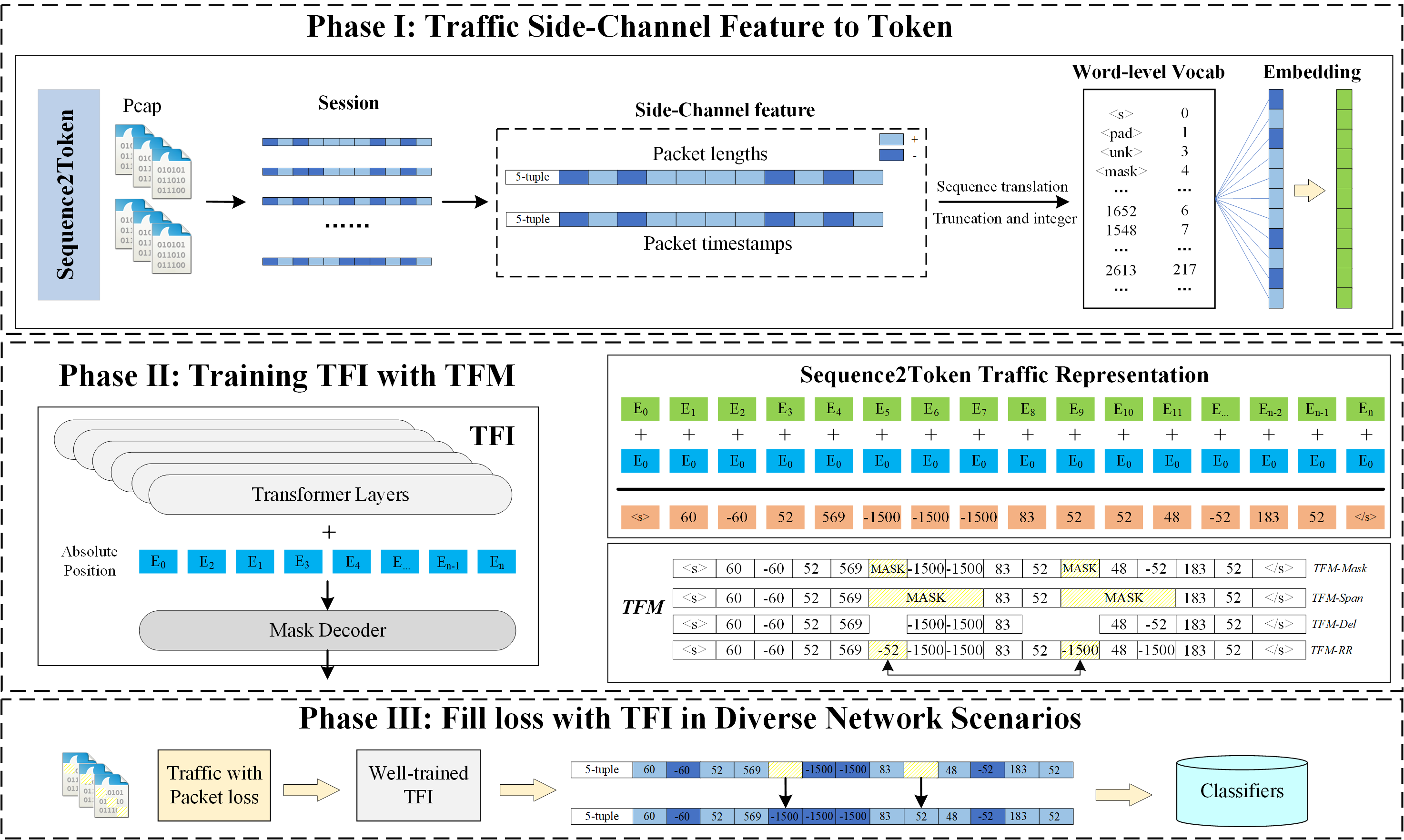
Nüwa: Enhancing Network Traffic Analysis with Pre-trained Side-channel Feature ImputationFaqi Zhao,Wenhao Li, Huaifeng Bao
2025.6.9
AI Security
Transactions on Dependable and Secure Computing (TDSC)
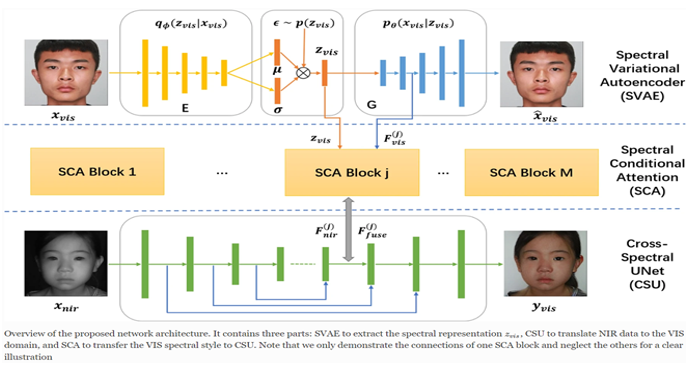
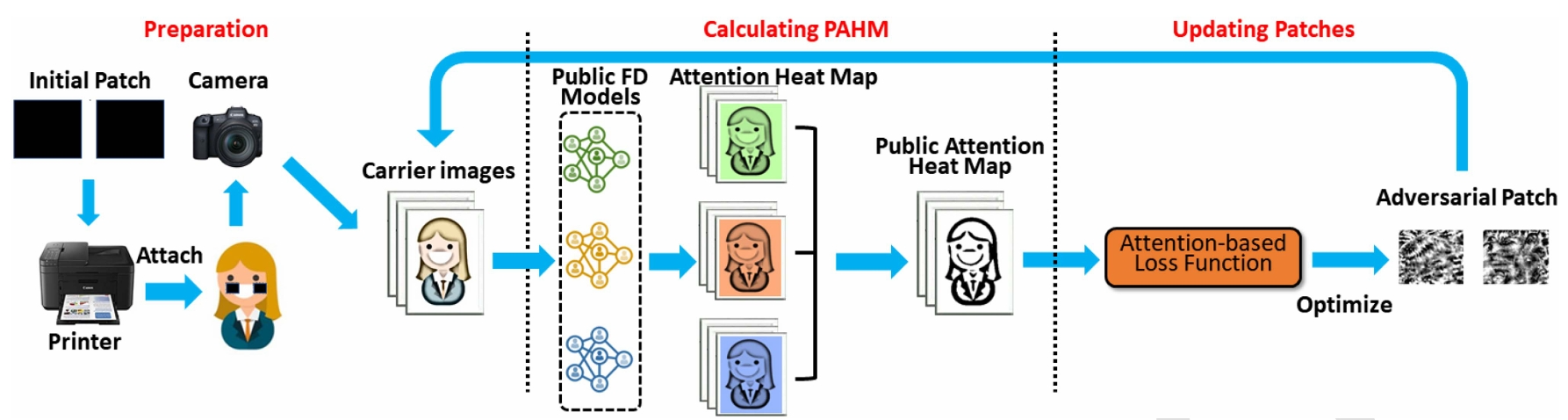
Got My “Invisibility” Patch: Towards Physical Evasion Attacks on Black-Box Face Detection SystemsDuohe Ma, Junye Jiang, Xiaoyan Sun, Zhimin Tang, Zhenchao Zhang, Kai Chen, Jun Dai
2025,06,07
Security
The 63rd Annual Meeting of the Association for Computational Linguistics (ACL2025)
Generate First, Then Sample: Enhancing Fake News Detection with LLM-Augmented Reinforced SamplingZhao Tong, Yimeng Gu, Huidong Liu, Qiang Liu, Shu Wu ,Haichao Shi and Xiao-Yu Zhang
2025.05.16
Security
International Conference On Intelligent Computing 2025 (ICIC2025)
Multimodal Test-Time Adaptation for Fake News DetectionZhao Tong, Xiang Yuan, Qiang Liu, Libin Han, Haichao Shi, Shu Wu and Xiao-Yu Zhang
2025.04.28
Security
2025International Conference On Intelligent Computing (ICIC 2025) (ICIC)
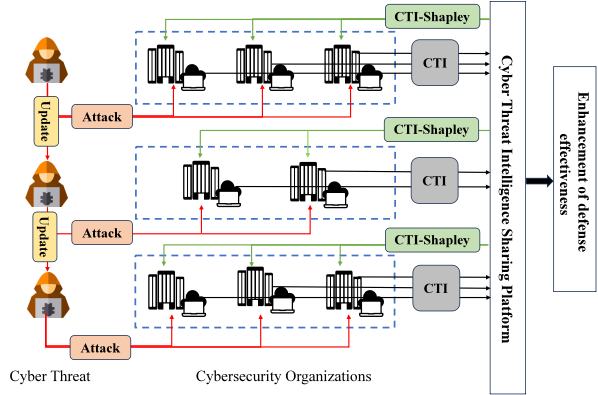
CTI-Shapley: An ATT&CK-Guided Enhanced Shapley Value Mechanism for Benefit Distribution in Cyber Threat Intelligence SharingXuanye Peng, Guangxaing Dai, Peng Wang
2025.4.28
Main Track
25th International Conference on Computational Science (ICCS)
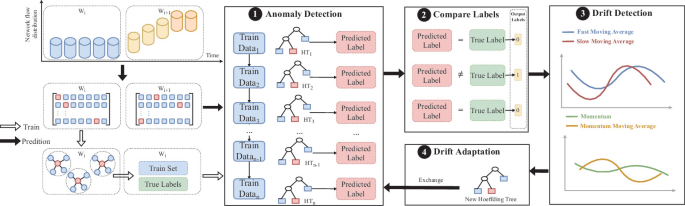
Dual Adaptive Windows toward Concept-Drift in Online Network Intrusion DetectionXiaowei Hu, Duohe Ma, Wen Wang and Feng Liu
2025.4.8
Security
International Joint Conference on Neural Networks 2025 (IJCNN2025)
R²FND: Reinforced Rationale Learning for Fake News Detection with LLMsZhao Tong, Yimeng Gu3, Haichao Shi, Qiang Liu, Shu Wu and Xiao-Yu Zhang
2025.04.01
Security
IEEE International Conference on Multimedia and Expo 2025 (ICME-2025)
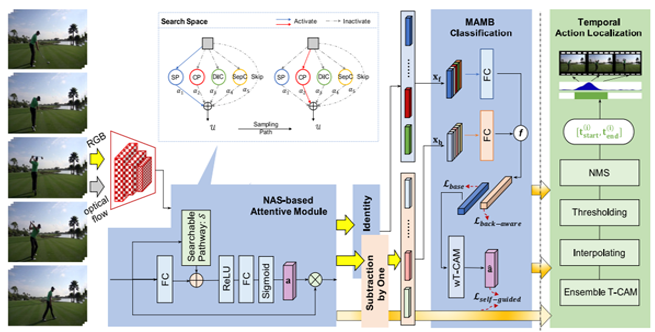
Concept-Centric Learning for Weakly-Supervised Temporal Sentence GroundingYaru Zhang, Haichao Shi and Xiao-Yu Zhang
2025.03.21
2025.3.19
Security
IEEE Transactions on Image Processing (TIP)
Global Cross-Entropy Loss for Deep Face RecognitionWeisong Zhao, Xiangyu Zhu, Haichao Shi, Member, IEEE, Xiao-Yu Zhang, Guoying Zhao, Zhen Lei
2025.02.17
Security
IEEE Internation Conference on Communications (ICC 2025)
Mirage: Real-time Network Traffic Evasion with Deep Reinforcement LearningWenhao Li, Jincai Zou, Zhuanxuan Li, Huamin Jin, Shuai Wang, Xiao-Yu Zhang
2025.01.18
Research Track
The 33rd IEEE/ACM International Conference on Program Comprehension (ICPC 2025) (ICPC)
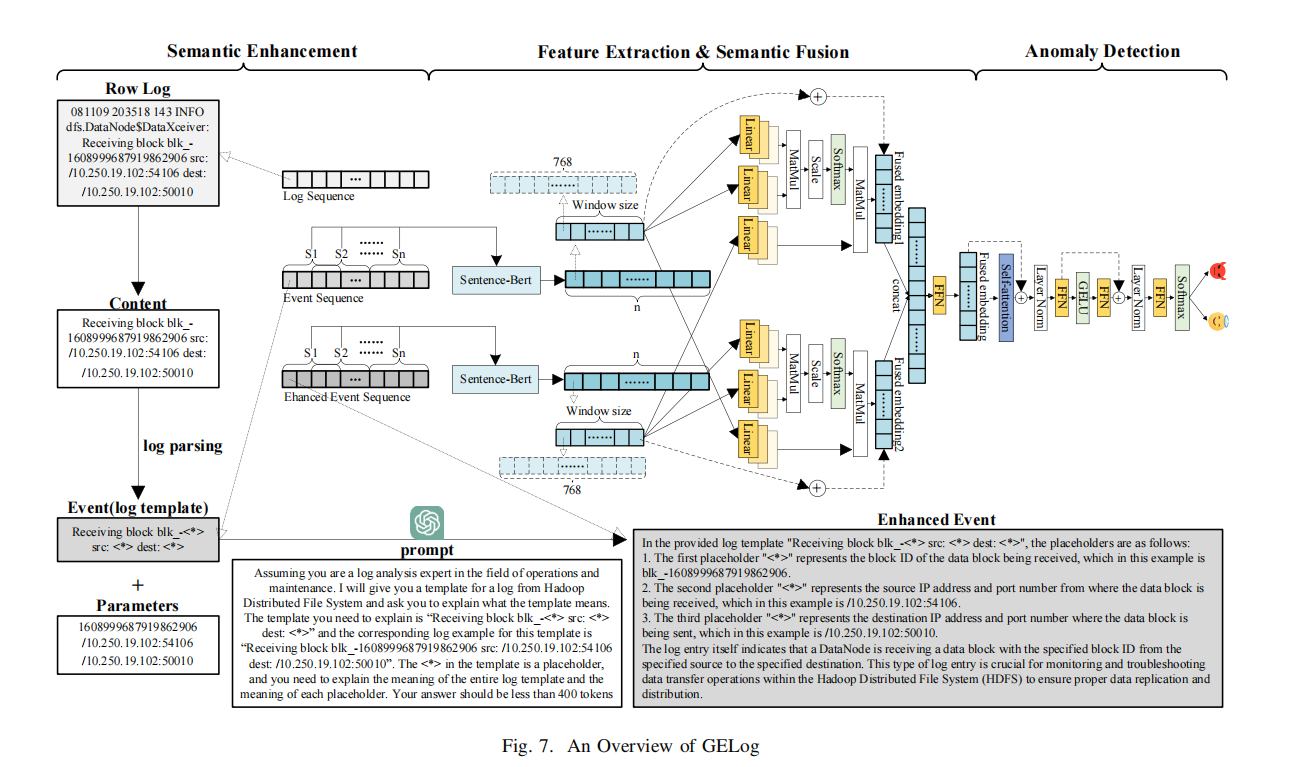
GELog: A GPT-Enhanced Log Representation Method for Anomaly DetectionXuWenwu, WangPeng, ShiHaichao, ZhouGuoqiao,YaoJunliang, ZhangXiaoyu
2025.1.13
2024
Security
2025 IEEE INTERNATIONAL CONFERENCE ON ACOUSTICS,SPEECH,AND SIGNAL PROCESSING (ICASSP 2025)
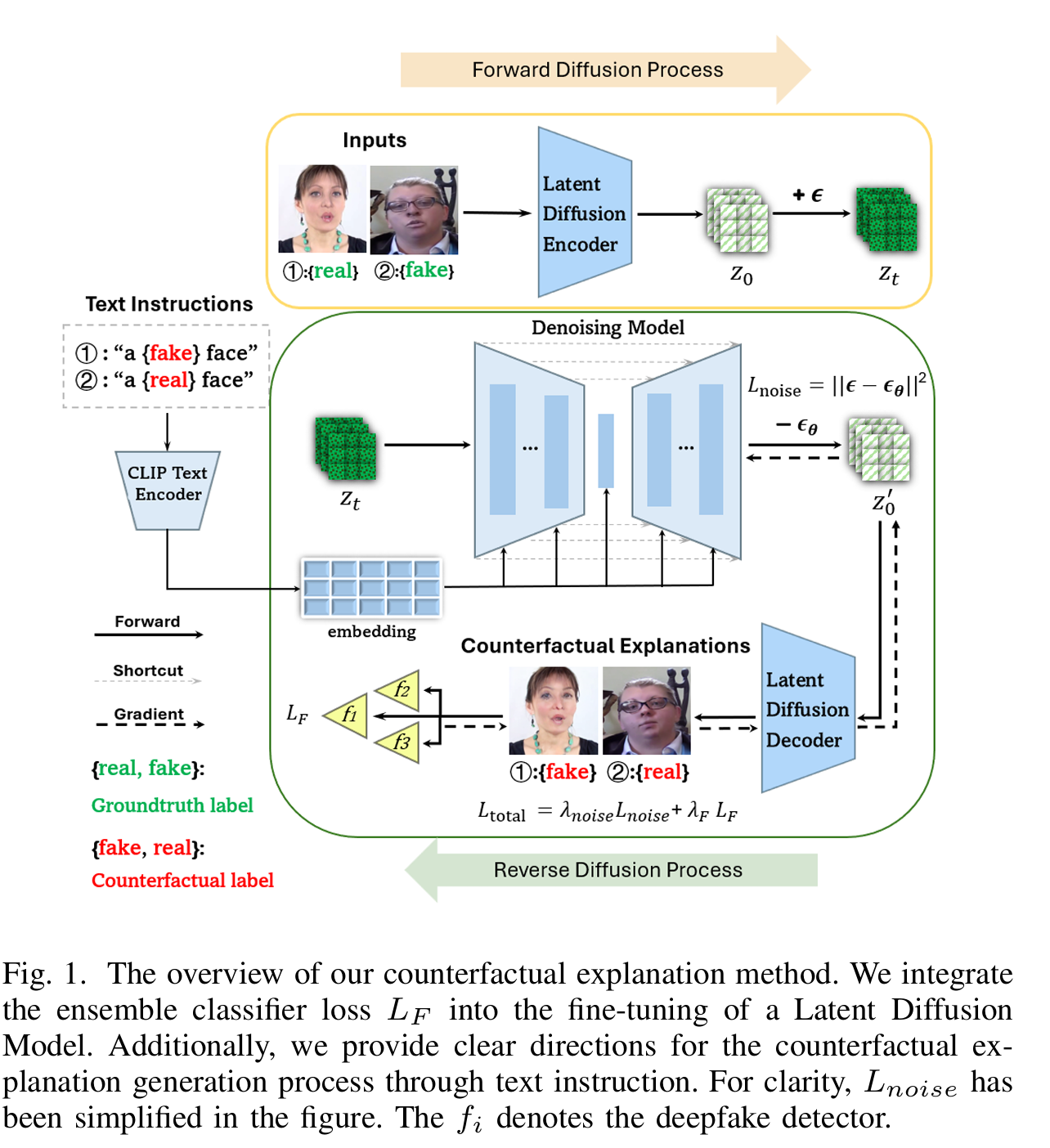
Unveiling Deepfakes with Latent Diffusion Counterfactual ExplanationsChen Yang, Bo Peng, Jing Dong, Xiaoyu Zhang
2024.12.21
Security
AAAI Conference on Artificial Intelligence (AAAI 2025)
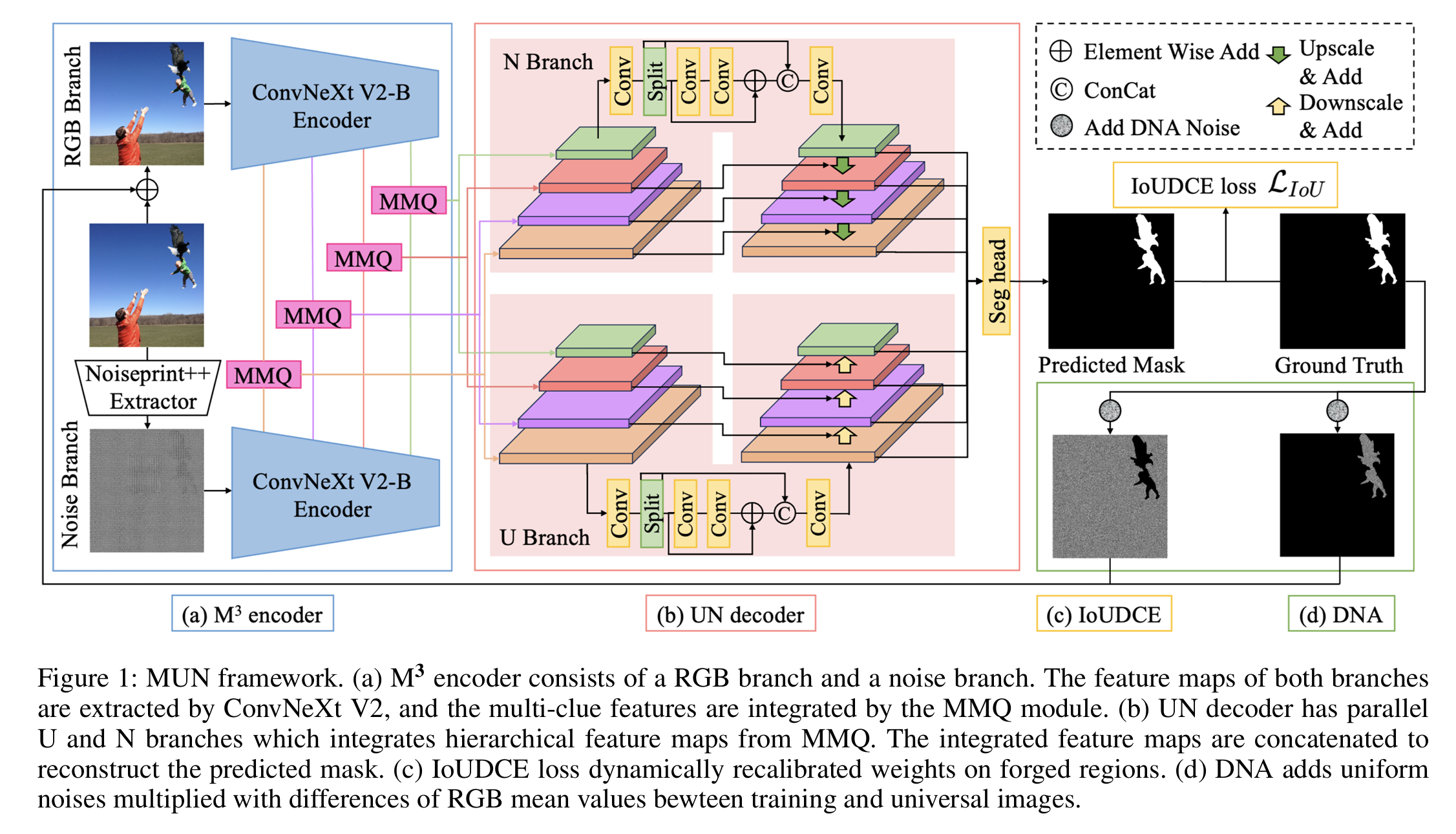
MUN:Image Forgery Localization Based on M3 Encoder and UN DecoderYaqi Liu, Shuhuan Chen, Haichao Shi, Xiao-Yu Zhang, Song Xiao, Qiang Cai
2024.12.10
AI Trust Track
23rd IEEE International Conference on Trust, Security and Privacy in Computing and Communications (Trust-com)
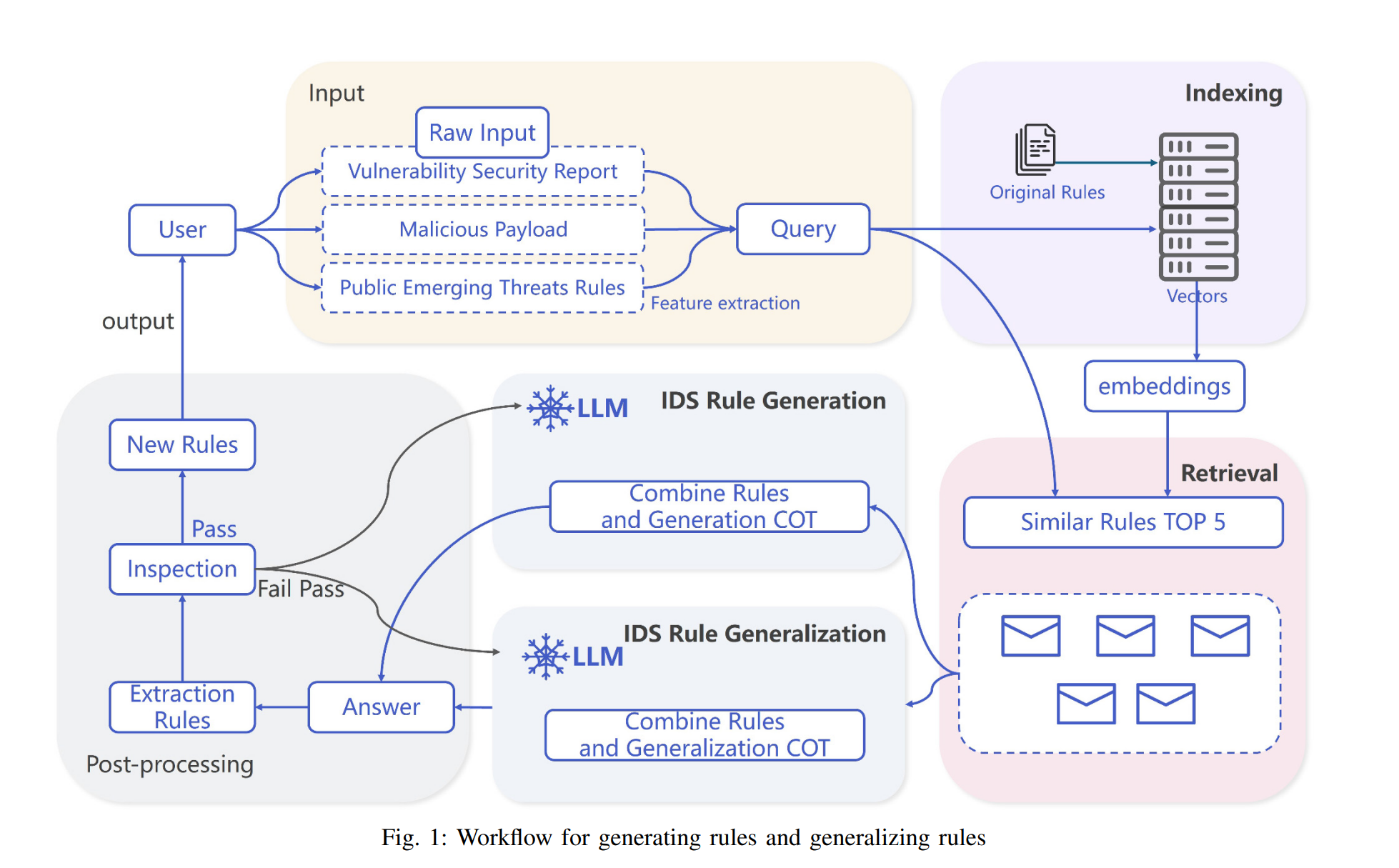
A LLM-based agent for the automatic generation and generalization of IDS rulesXiaowei Hu, Haoning Chen, Huaifeng Bao, Wen Wang, Feng Liu, Guoqiao Zhou, Peng Yin
2024.11.1
Research Track
International Conference on Information Security and Cryptology (ICISC 2024) (ICISC)
Pre-trained Language Models for Alert Aggregation: Limitations and OpportunitiesXuWenwu, WuPengyi, WangPeng,ZhouGuoqiao, ZhaiLidong
2024.10.30
Security
IEEE International Conference on Ubiquitous Intelligence and Computing(UIC)
A Vulnerability-Driven Gym for Training Autonomous Cyber Agents with Reinforcement LearningWeixia Cai, Huashan Chen, Han Miao, Feng Liu, Yong Zhang, Xiaojia Yang
2024.9.26
Security
2024 International Conference On Intelligent Computing (ICIC 2024) (ICIC)
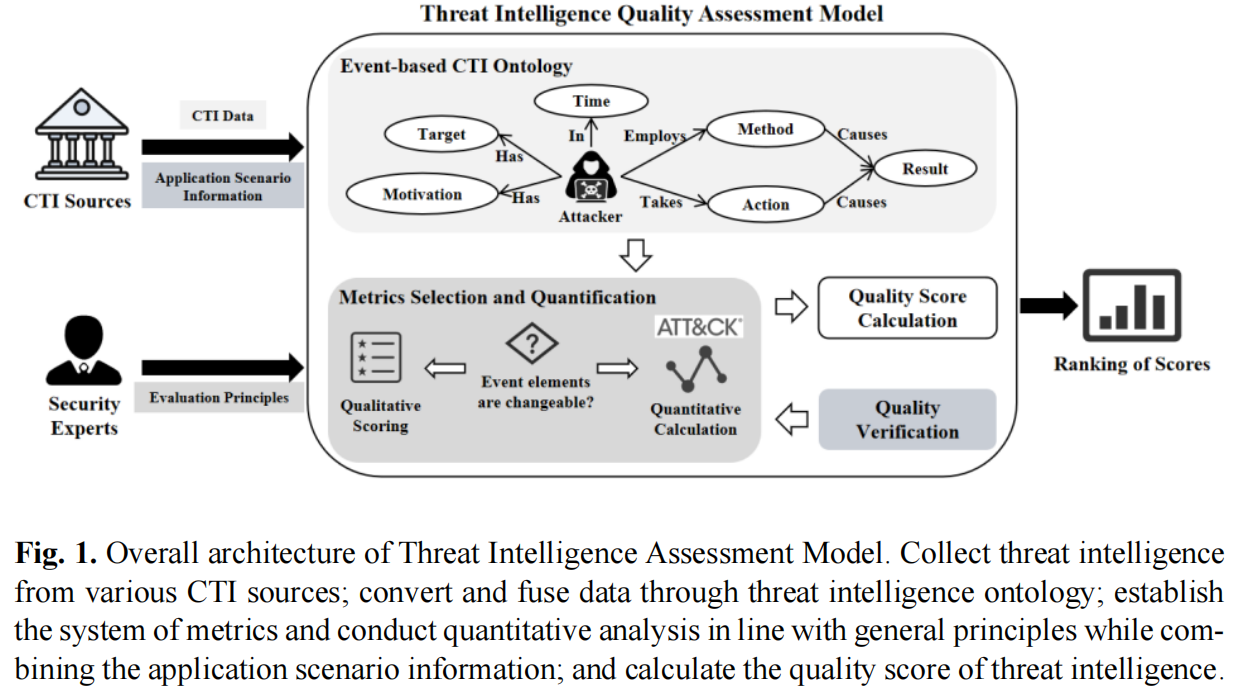
Threat Intelligence Quality Assessment Model Based on ATT&CK Framework for Multiple Application ScenariosGuangxiang Dai, Peng Wang, Pengyi Wu
2024.8.20
Security
IEEE International Joint Conference on Biometrics (IJCB)
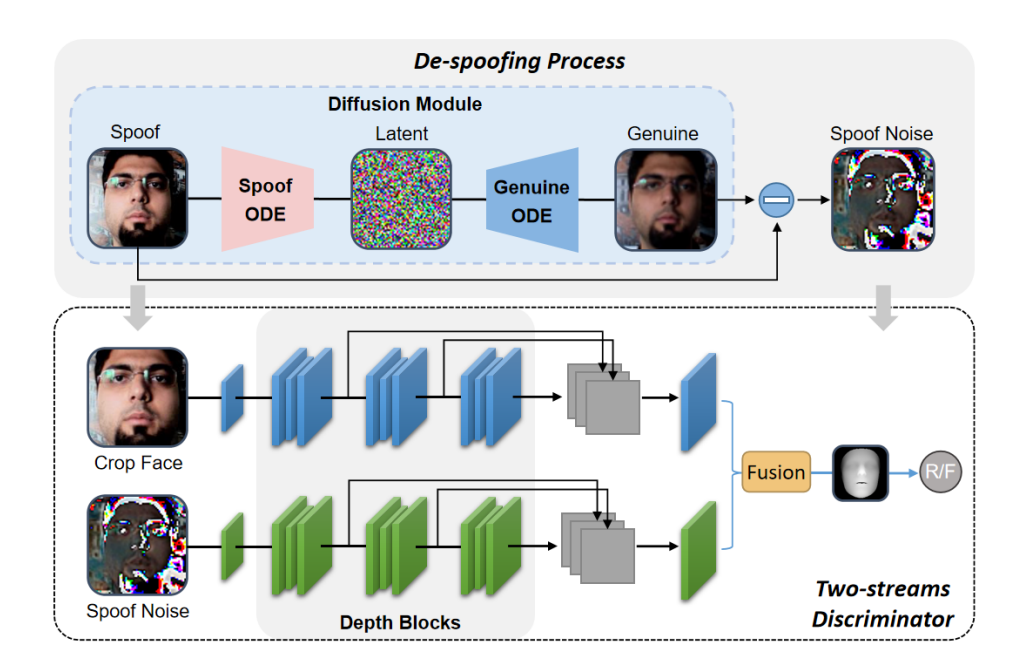
Modeling Spoof Noise by De-spoofing Diffusion and its Application in Face Anti-spoofingBin Zhang, Xiangyu Zhu, Xiaoyu Zhang, Zhen Lei
2024.6.17
Security
Pattern Recognition
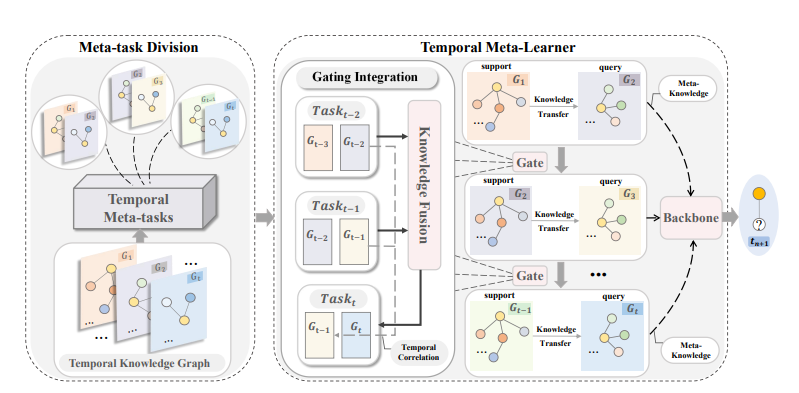
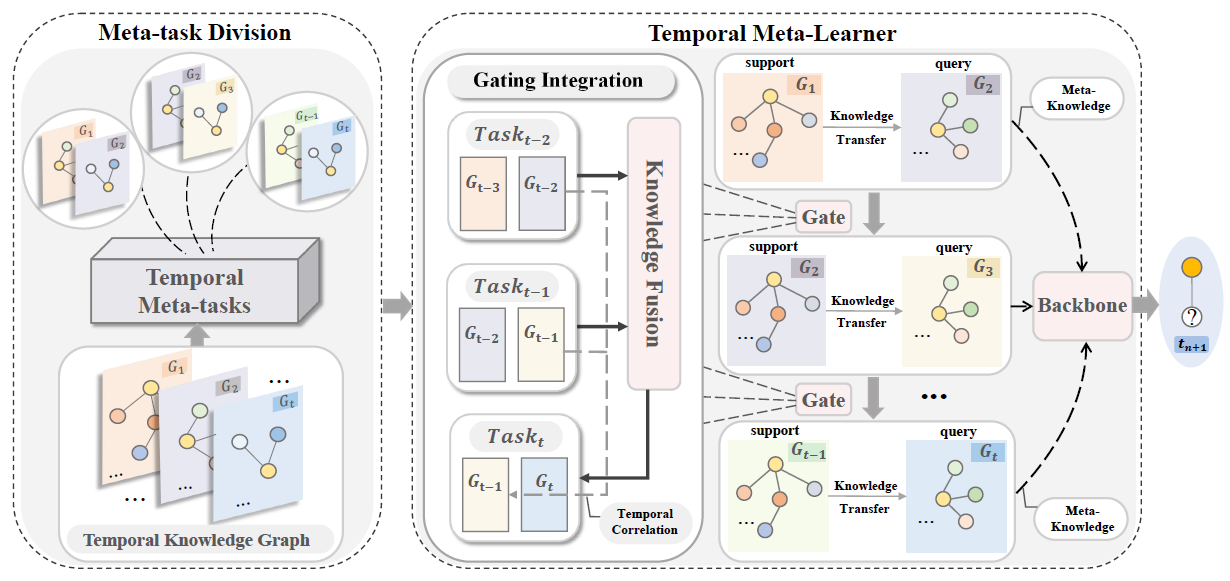
MetaTKG++: Learning evolving factor enhanced meta-knowledge for temporal knowledge graph reasoningYuwei Xia, Mengqi Zhang, Qiang Liu, Shu Wu, Xiao-Yu Zhang
2024.5.23
Security
Findings of the Association for Computational Linguistics ACL 2024
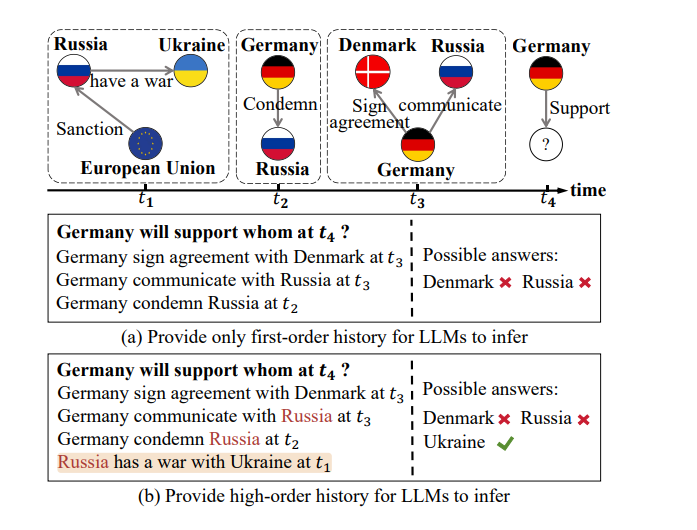
Chain-of-History Reasoning for Temporal Knowledge Graph ForecastingYuwei Xia, Ding Wang, Qiang Liu, Liang Wang, Shu Wu, Xiao-Yu Zhang
2024.5.16
Security
Intelligent Computing Technology and Applications
Semantics Fusion of Hierarchical Transformers for Multimodal Named Entity RecognitionZhao Tong, Qiang Liu, Haichao Shi, Yuwei Xia, Shu Wu & Xiao-Yu Zhang
2024.5.19
Security
IEEE International Conference on Multimedia and Expo (ICME 2024)
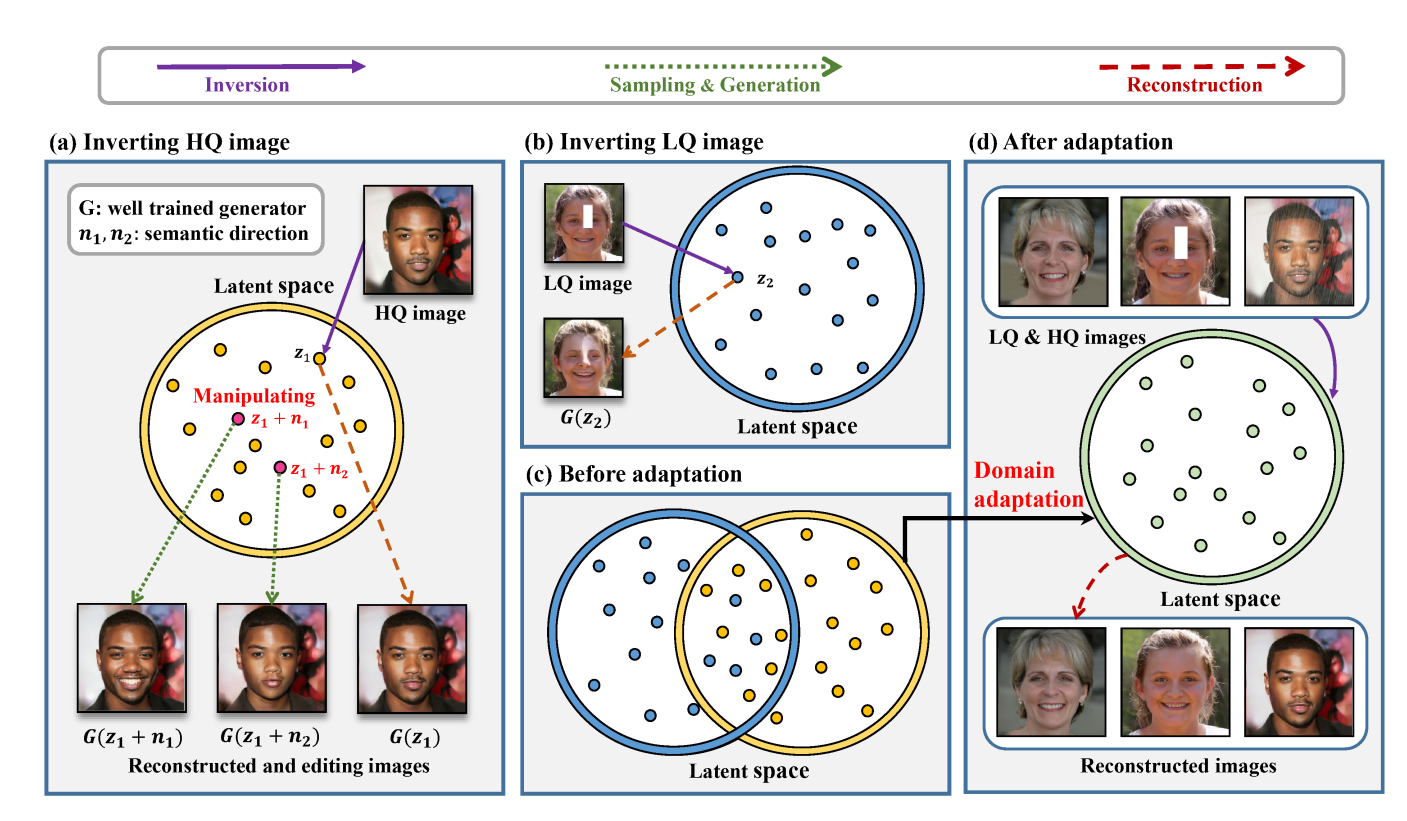
GAN Inversion for Image Editing via Unsupervised Domain AdaptationSiyu Xing, Chen Gong, Hewei Guo, Xiao-Yu Zhang, Xinwen Hou, Yu Liu
2024.3.13
Security
International Journal of Computer Vision (IJCV)
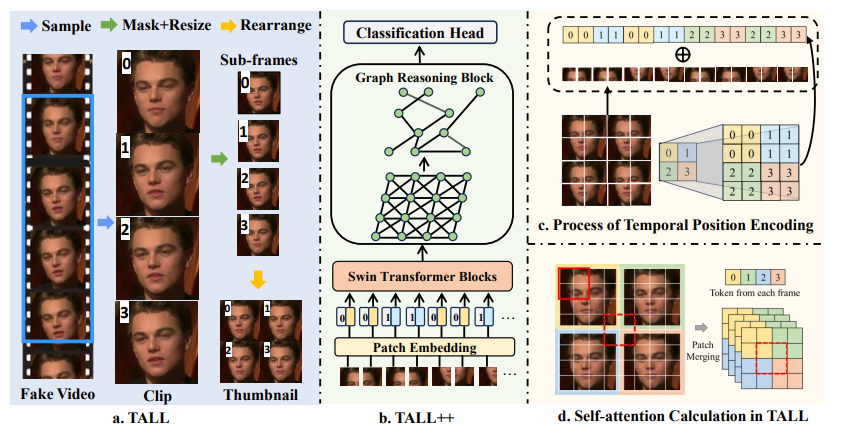
Learning Spatiotemporal Inconsistency via Thumbnail Layout for Face Deepfake DetectionYuting Xu, Jian Liang, Lijun Sheng, Xiao-Yu Zhang
2024.3.13
Network Security
The 24th International Conference on Computational Science (ICCS 2024)
A Framework for Intelligent Generation of Intrusion Detection Rules Based on Grad-CAMXingyu Wang
2024.05
2023
Computer Vision
The 6th Chinese Conference on Pattern Recognition and Computer Vision (PRCV 2023)
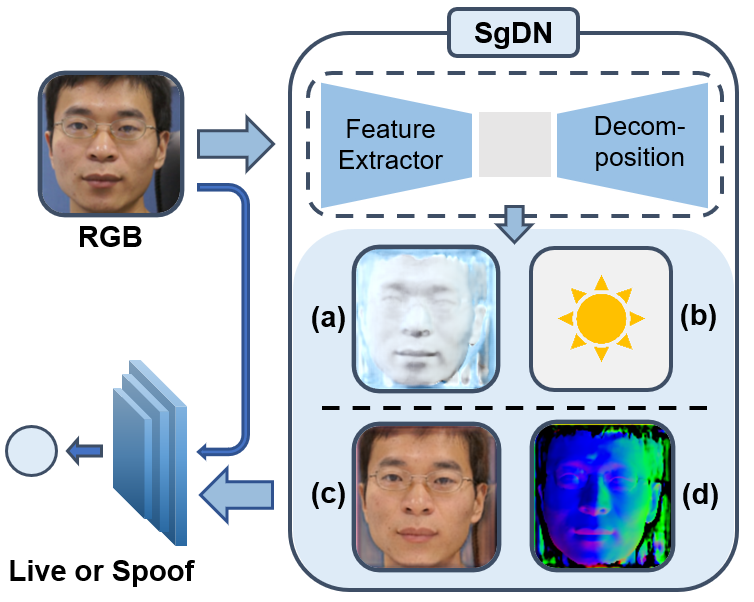
Spoof-guided Image Decomposition for Face Anti-spoofingBin Zhang, Xiangyu Zhu, Xiaoyu Zhang, Shukai Chen, and Zhen Lei
2023.08.23
Computer Vision
IJCB 2023
Modeling Spoof Noise by De-spoofing Diffusion and its Application in Face Anti-spoofingBin Zhang, etc.
Network Security
Globecom 2023
Towards Open-Set APT Malware Classification under Few-Shot SettingHuaifeng Bao, etc.
Network Security
SciSec 2023 2023
AST2Vec: A Robust Neural Code Representation for Malicious PowerShell DetectionHan Miao, etc.
Data Mining
29TH ACM SIGKDD CONFERENCE ON KNOWLEDGE DISCOVERY AND DATA MINING (KDD 2023)
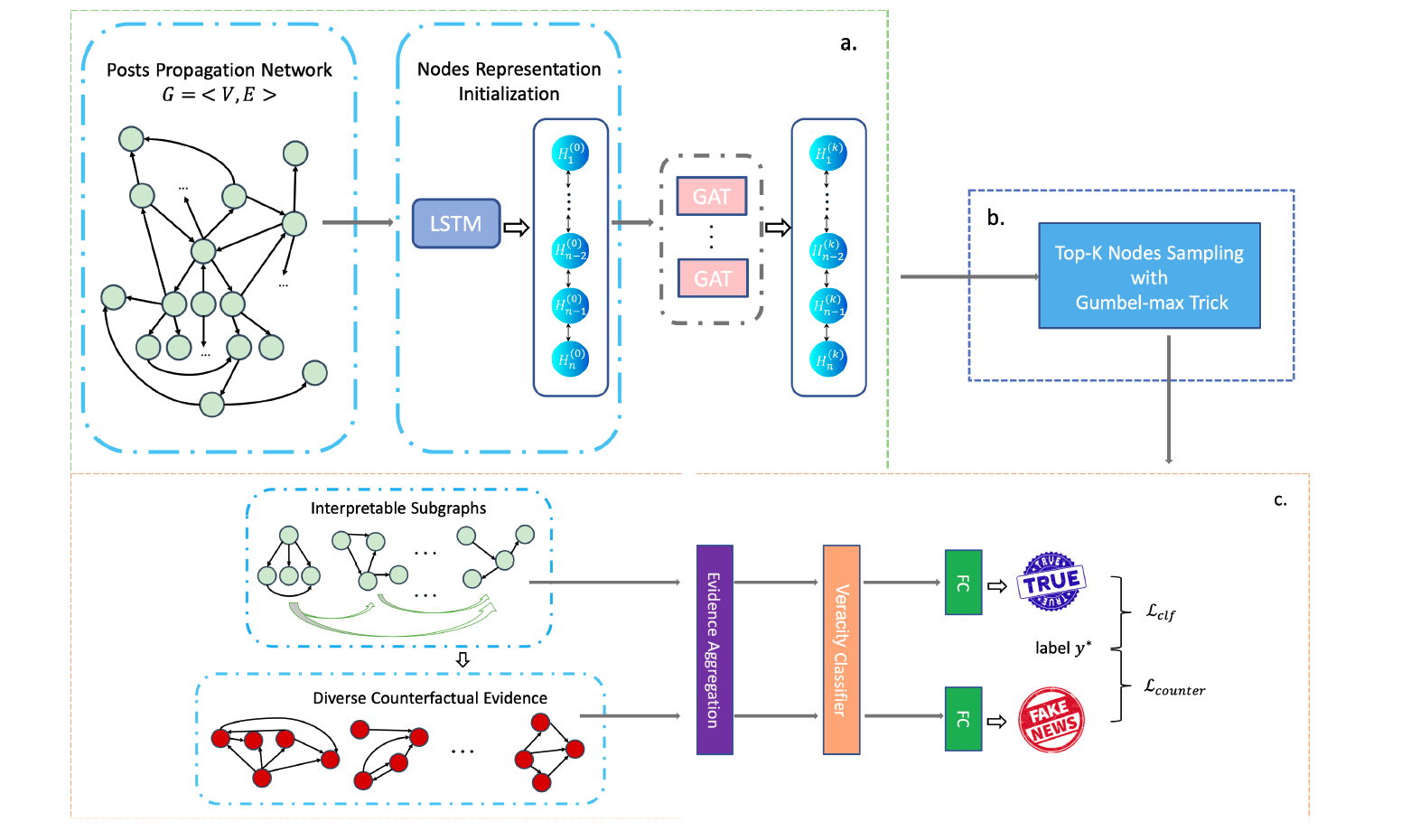
Rumor Detection with Diverse Counterfactual EvidenceKaiwei Zhang, Junchi Yu, Haichao Shi, Jian Liang, Xiao-Yu Zhang*
2023.05.17
Network Security
IEEE Transactions on Information Forensics and Security. (TIFS) 2023
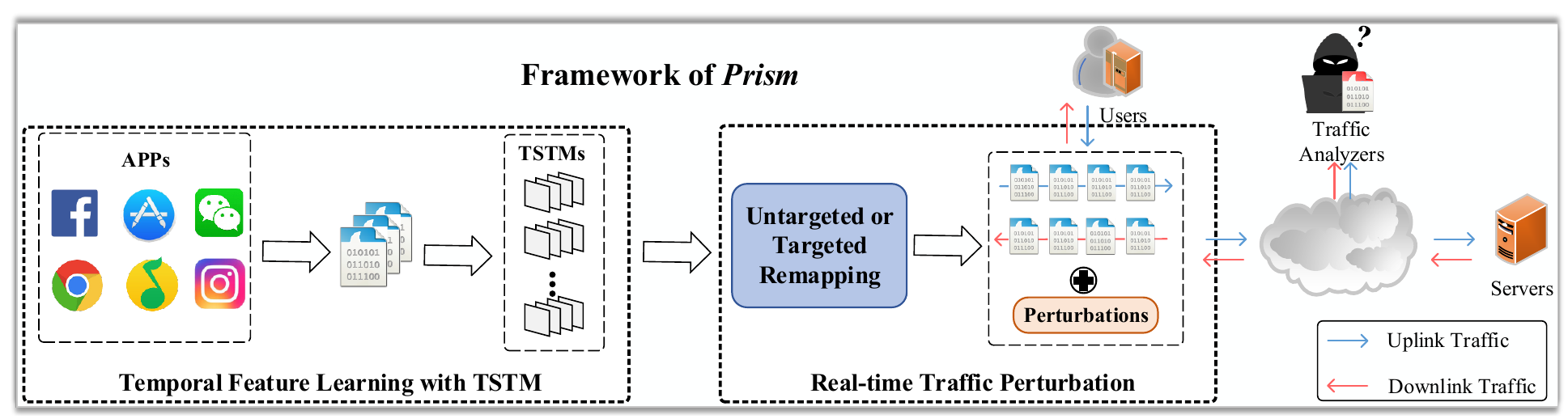
Prism: Real-Time Privacy Protection Against Temporal Network Traffic AnalyzersWenhao Li, Xiao-Yu Zhang*, Huaifeng Bao, Binbin Yang, Zhaoxuan Li, Haichao Shi, Qiang Wang
2023.04.13
Computer Vision
International Conference on Computational Science. (ICCS 2023)
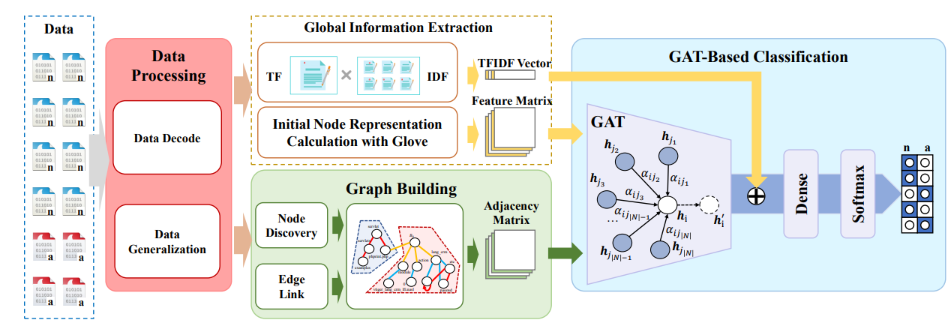
Payload Level Graph Attention Network for Web Attack Traffic DetectionHuaifeng Bao, Wenhao Li, Xingyu Wang, Zixian Tang, Qiang Wang, Wen Wang, and Feng Liu
2023.04.06
Computer Vision
IEEE Transactions on Information Forensics and Security. (TIFS) 2023
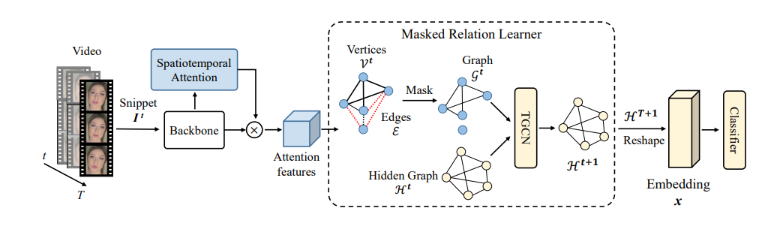
Masked Relation Learning for DeepFake DetectionZiming Yang, Jian Liang, Yuting Xu, Xiao-Yu Zhang, and Ran He
2023.02.14
Computer Vision
IEEE Transactions on Information Forensics and Security. (TIFS) 2023
Masked Relation Learning for DeepFake DetectionZiming Yang, Jian Liang, Yuting Xu, Xiao-Yu Zhang, and Ran He
2023.02.14
Computer Vision
IEEE Transactions on Image Processing. (TIP) 2023
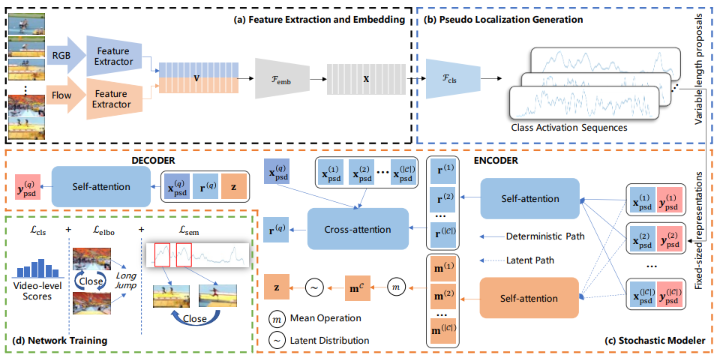
StochasticFormer: Stochastic Modeling for Weakly Supervised Temporal Action LocalizationHaichao Shi; Xiao-Yu Zhang and Changsheng Li
2023.02.11
2022
Computer Vision
The 27th AAAI Conference on Artificial Intelligence (AAAI-2022)
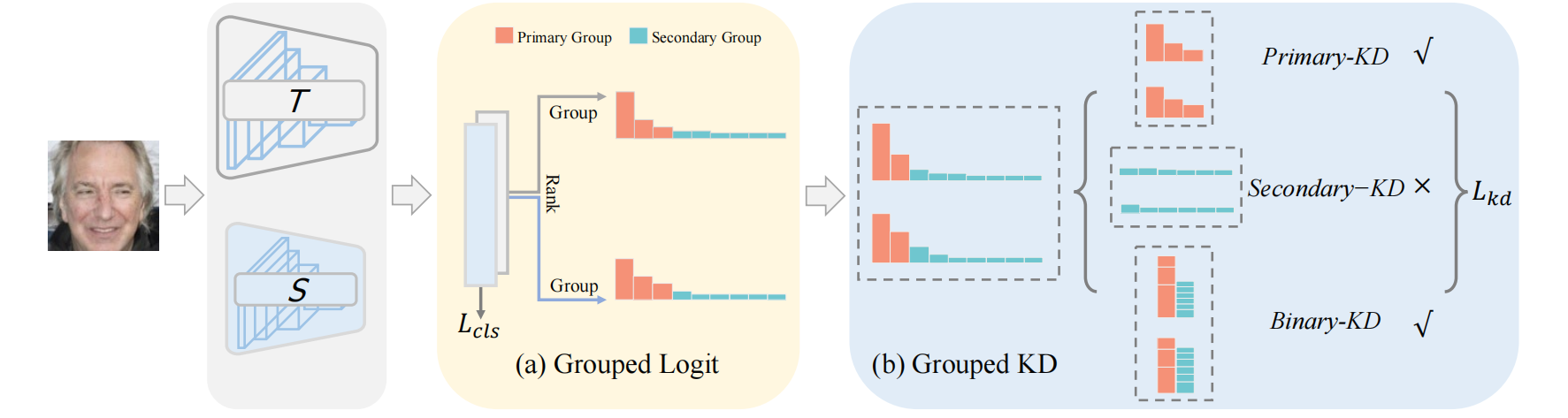
Grouped Knowledge Distillation for Deep Face RecognitionWeisong Zhao, Xiangyu Zhu, Kaiwen Guo, Xiao-Yu Zhang* and Zhen Lei
2022.11.19
Network Security
The 24th IEEE International Conference on High Performance Computing and Communications (HPCC-2022)
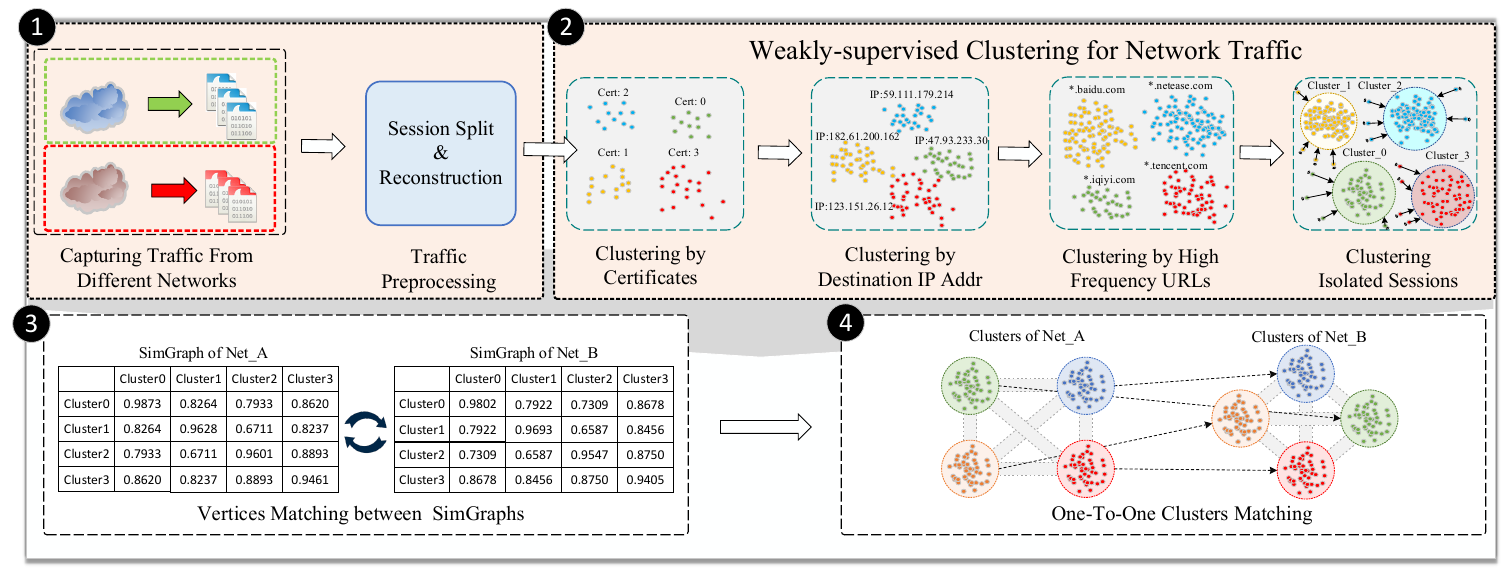
A Glimpse of the Whole: Detecting Few-shot Android Malware Encrypted Network TrafficWenhao Li, Xiao-Yu Zhang*, Huaifeng Bao, Qiang Wang, Haichao Shi and Zhaoxuan Li
2022.10.24
Network Security
IEEE/ACM Transcations on Networking. (ToN) 2022
ProGraph: Robust Network Traffic Identification with Graph PropagationWenhao Li, Xiao-Yu Zhang*, Huaifeng Bao, Haichao Shi and Qiang Wang
2022.10.15
Knowledge Graph
Proceedings of the 2022 Conference on Empirical Methods in Natural Language Processing. (EMMLP) 2022
MetaTKG: Learning Evolutionary Meta-Knowledge for Temporal Knowledge Graph ReasoningYuwei Xia, Mengqi Zhang, Qiang Liu*, Shu Wu and Xiao-Yu Zhang
2022.10.07
Network Security
Computer Networks. (CN) 2022
Robust Network Traffic Identification with Graph MatchingWenhao Li, Xiao-Yu Zhang*, Baohuai Feng, Qiang Wang and Zhaoxuan Li
2022.09.17
Network Security
Military Communications Conference (MILCOM), 2022
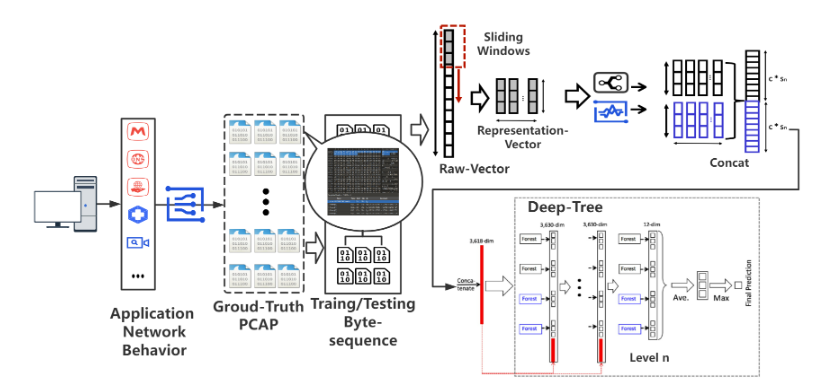
High-Efficient and Few-Shot Adaptive Encrypted Traffic Classification With Deep TreeQiang Wang, Wenhao Li, Huaifeng Bao, Zixian Tang, Wen Wang*, Feng Liu, Lingyun Ying.
2022.09.10
Computer Vision
Pattern Recognition. (PR) 2022
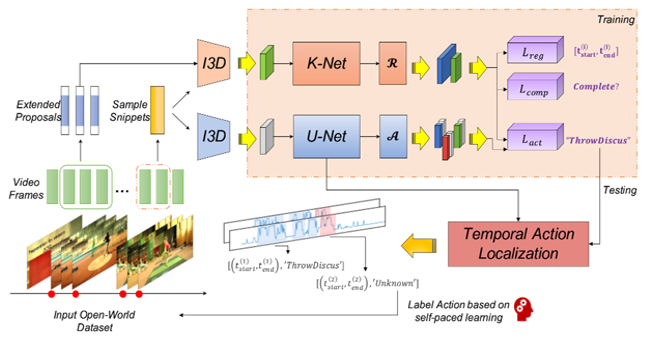
OW-TAL: Learning Unknown Human Activities for Open-World Temporal Action LocalizationYaru Zhang, Xiao-Yu Zhang and Haichao Shi
2022.09.04
Computer Graphics
The IEEE International Conference on Multimedia & Expo (ICME2022)
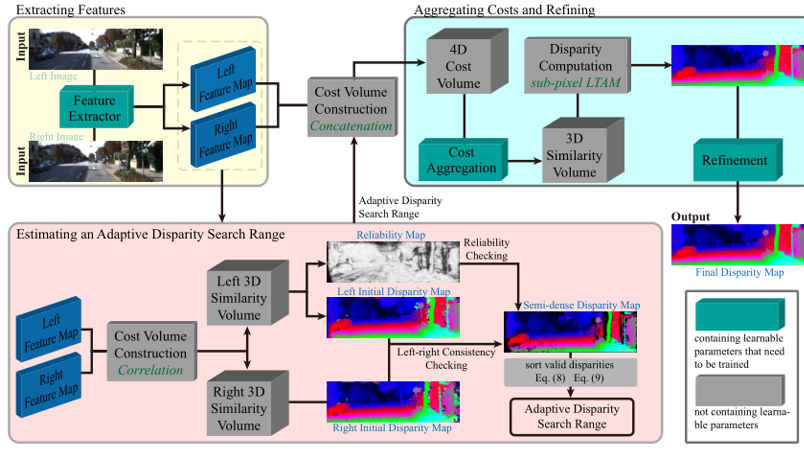
A Novel Stereo Matching Pipeline with Robustness and Unfixed Disparity Search RangeJiazhi Liu and Feng Liu
2022.08.26
Computer Vision
ACM MM 2022
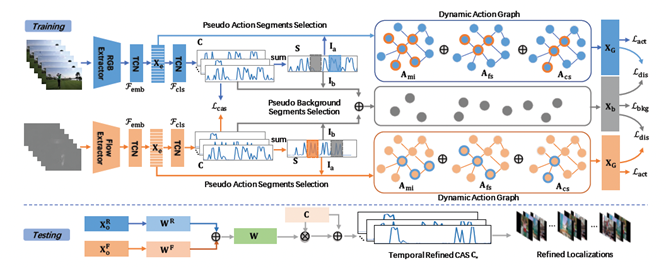
Dynamic Graph Modeling for Weakly-Supervised Temporal Action LocalizationHaichao Shi, Xiao-Yu Zhang, Changsheng Li, Lixing Gong, Yong Li, Yongjun Bao
2022.06.30
Computer Vision
IEEE Transactions on Image Processing. (TIP) 2022
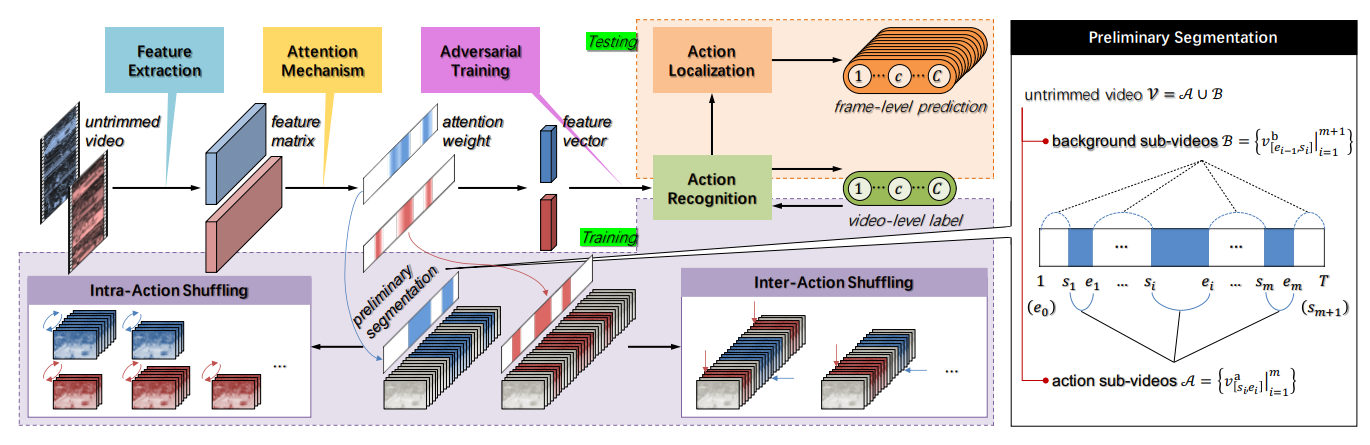
Action Shuffling for Weakly Supervised Temporal LocalizationXiao-Yu Zhang; Haichao Shi; Changsheng Li and Xinchu Shi
2022.06.13
Computer Vision
Machine Intelligence Research. (MIR) 2022
TwinNet: Twin Structured Knowledge Transfer Network for Weakly Supervised Action LocalizationXiao-Yu Zhang, Haichao Shi*, Changsheng Li, Lixin Duan
2022.05.12
Computer Graphics
ACM Transactions on Multimedia Computing, Communications, and Applications (TOMM) 2022
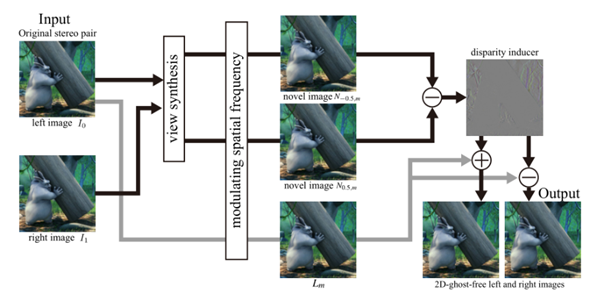
Modified 2D-Ghost-Free Stereoscopic Display with Depth-of-Field EffectsJiazhi Liu and Feng Liu
2022.05.12
2022.04.11
Computer Vision
IEEE Transactions on Information Forensics and Security. (TIFS) 2022
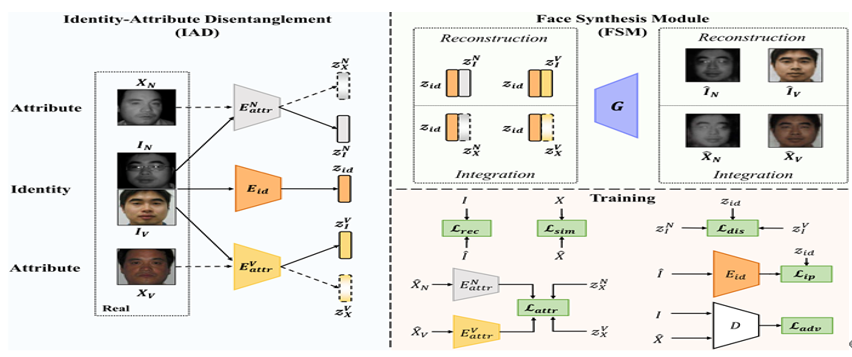
Heterogeneous Face Recognition via Face Synthesis with Identity-Attribute DisentanglementZiming Yang, Jian Liang, Chaoyou Fu, Mandi Luo and Xiao-Yu Zhang
2022.03.17
Computer Graphics
26th International Conference on Pattern Recognition (ICPR2022)
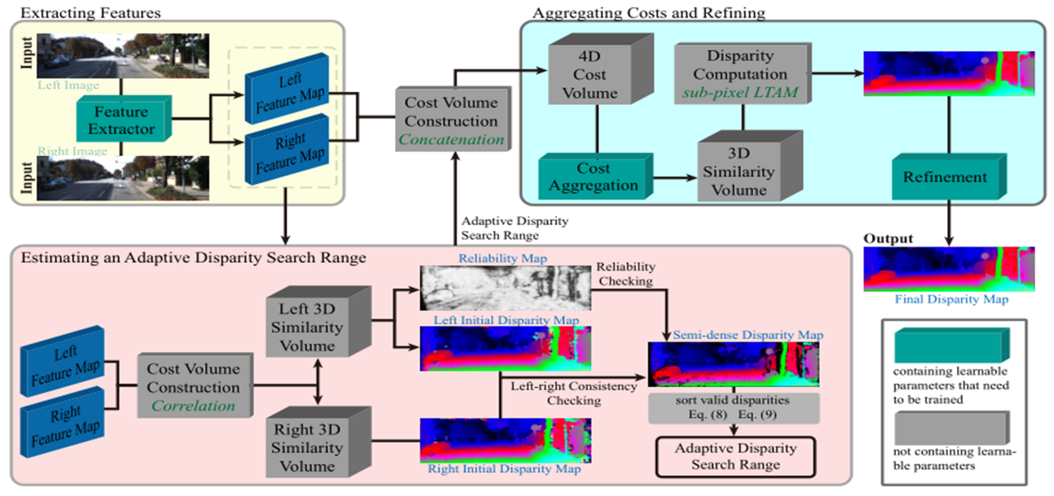
Robust Stereo Matching with an Unfixed and Adaptive Disparity Search RangeJiazhi Liu and Feng Liu
2022.03.09
Network Security
International Conference on Computational Science. (ICCS 2022)
AMDetector: Detecting Large-scale and Novel Android Malware Traffic with Meta-learningWenhao Li, Xiao-Yu Zhang, Huaifeng Bao and Lin Li.
2022.03.04
Network Security
International Conference on Computational Science. (ICCS 2022)
GBLNet: Detecting Intrusion Traffic with Multi-granularity BiLSTMWenhao Li and Xiao-Yu Zhang.
2022.03.04
2021
Computer Vision
Computer Vision and Image Understanding.(CVIU) 2021
SAPS: Self-Attentive Pathway Search for weakly-supervised action localization with background-action augmentationXiao-Yu Zhang, Yaru Zhang, Haichao Shi and Jing Dong
2021.07.24
Computer Vision
International Journal of Computer Vision .(IJCV) 2021
Lamp-hq: A large-scale multi-pose high-quality database and benchmark for nir-vis face recognitionAijing Yu, Haoxue Wu, Huaibo Huang, Zhen Lei and Ran He
2021.02.12
Malware Detection
SciSec 2021: Science of Cyber Security. (SciSec 2021)
Mining Trojan Detection Based on Multi-dimensional Static FeaturesZixian Tang, Qiang Wang, Wenhao Li, Huaifeng Bao, Feng Liu, and Wen Wang.
2021.06.04
Network Security
International Conference on Computational Science. (ICCS 2021)
HSLF: HTTP Header Sequence based LSH fingerprints for Application Traffic ClassificationZixian Tang, Qiang Wang, Wenhao Li, Huaifeng Bao, Feng Liu, and Wen Wang.
2021.03.04
Computer Vision
Pattern Recognition. (PR) 2022
Weakly-supervised Action Localization Via Embedding-modeling Iterative OptimizationXiao-Yu Zhang, Haichao Shi, Changsheng Li, Peng Li, Zekun Li, Peng Ren.
2021.01.16
2020
Computer Vision
AAAI 2020
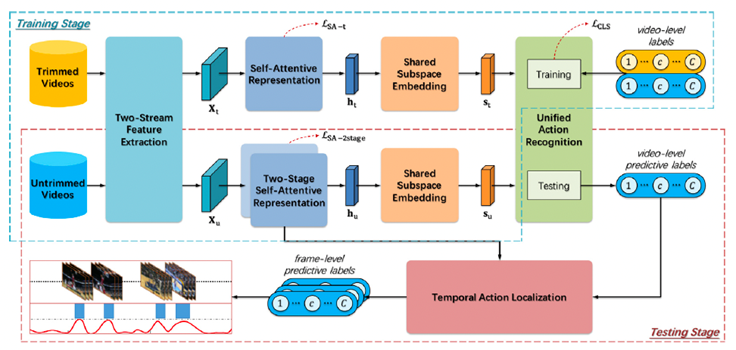
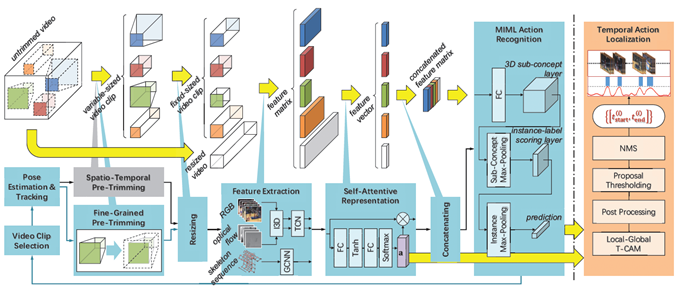
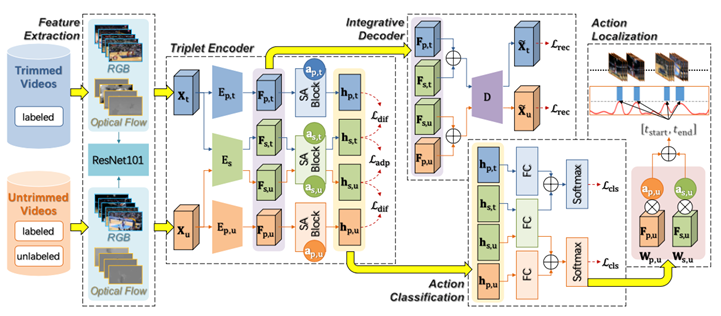
Multi-Instance Multi-Label Action Recognition and Localization Based on Spatio-Temporal Pre-Trimming for Untrimmed VideosXiao-Yu Zhang, Haichao Shi, Changsheng Li, Peng Li
2020.04.03
Computer Vision
IEEE Transactions on Neural Networks and Learning Systems. (TNNLS) 2020
AdapNet: Adaptability Decomposing Encoder-Decoder Network for Weakly Supervised Action Recognition and LocalizationXiao-Yu Zhang, Changsheng Li, Haichao Shi*, Xiaobin Zhu, Peng Li, Jing Dong
2020.01.23
2019
Computer Vision
AAAI 2019
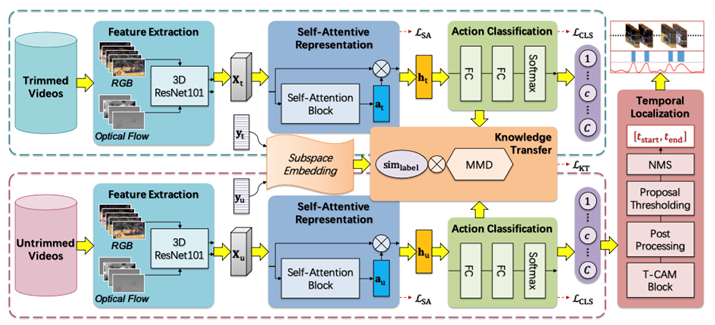
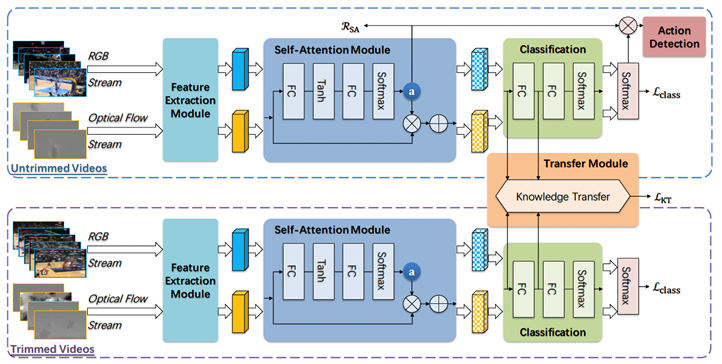
Learning Transferable Self-attentive Representations for Action Recognition in Untrimmed Videos with Weak SupervisionXiao-Yu Zhang, Haichao Shi, Changsheng, Kai Zheng, Xiaobin Zhu, Lixin Duan
2019.07.17
Computer Vision
Neurocomputing 2019
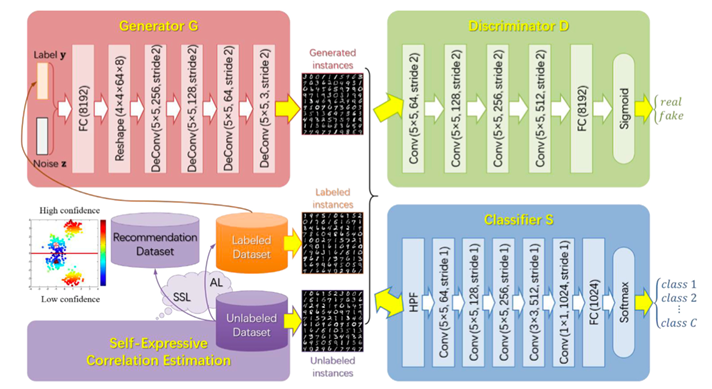
Active Semi-supervised Learning Based on Self-expressive Correlation with Generative Adversarial NetworksXiao-Yu Zhang, Haichao Shi, Xiaobin Zhu, Peng Li
2019.01.08
2018
Computer Vision
AAAI 2019
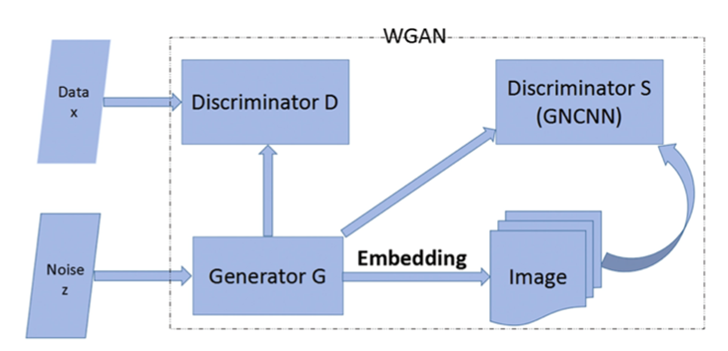
SSGAN: Secure Steganography Based on Generative Adversarial NetworksHaichao Shi, Jing Dong, Wei Wang, Yinlong Qian, Xiao-Yu Zhang*
2018.05.10


Wenhao Li-Tifs.jpg)
Jipeng Liu MM.png)
Zhao Tong-ACL2025.jpg)
Zhao Tong-ICIC2025.jpg)
Zhao Tong-IJCNN2025.jpg)
Yaru zhang ICME2025.jpg)
WeiSong Zhao TIP.jpg)
Wenhao Li ICC.jpg)